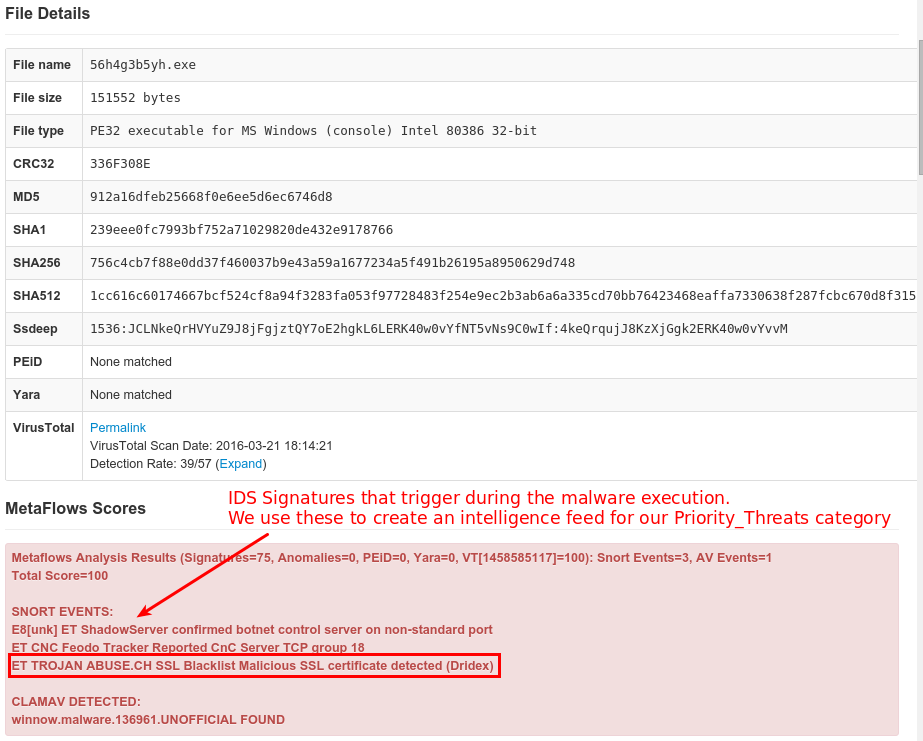
Since mid-February, security researchers have been encountering Locky, the latest ransomware tool in the adversary’s arsenal. The engineers at MetaFlows observe Locky primarily in email attachments that are processed using the MetaFlows sandbox. On networks being monitored by MetaFlows sensors, the engineers are able to take samples of inbound .zip email attachments and send them to a Cuckoo Sandbox to be processed. The sandbox runs the sample in a virtual machine and is able to detect malicious behavior. Often malware tries to evade detection, but since Locky is trying to get noticed by the user anyway, it is not subtle. Locky typically triggers over a dozen indicators of compromise and IDS signatures on the sandbox and therefore, is almost impossible to miss.
MetaFlows has seen consistent spam campaigns over the last month that deliver zipped JavaScript files that Windows is designed to execute by default with its native wscript.exe. The files, when executed by the user, appear to do nothing at first. This is a bad sign. Within moments a secondary payload is fetched, encryption has begun, and command and control beaconing has been performed in the background. Once it is done, the user will be greeted with the typical ransomware demands webpage, image, and wallpaper.


The spam campaigns use short, simple subject lines, or they include only “Re:” or “Fw:”. They are often appeals to business or tax related concerns, and the body is usually curt with a reasonable request to review the attachment and respond. These emails frequently include a legitimate appearing signature and use appropriate spelling and grammar. It is easy to see that people who are not constantly on guard about these issues could easily be tricked into opening the file. In the example below, the target could be concerned that they or their business missed a legitimate payment, or knowing that they have no business with “China Information Technology, Inc.,” they may open it to investigate why they have been billed.

The engineers at MetaFlows also collect statistics on the email subjects used to lure victims into opening the attachments, these are part of the Weekly Statistics page. The subjects vary from scare tactics, to just curiosity, to near gibberish, but they are rarely outlandish or over-the-top as spam quite often is. Not all of these are Locky, but the vast majority those that have made an appearance this week are.
Enterprises can make themselves less of a target by employing a two-layer approach. Investing in an IDS such as MetaFlows that will detect the inbound file, and recognize the infection behavior of a compromised system is the first layer. Given the current view on the spam campaigns distributing ransomware, the best solution is user education. Staff members should be approached, reminded regularly of this problem, and ideally possess some healthy paranoia about opening email attachments unless they absolutely know the sender. Also, even though .doc and other common files can be vectors for infection as well. Most users have no reason to ever open a .js with a strange icon.
The next layer consists of getting user files out of the path of Locky and other ransomware. While the campaigns we are seeing are spam based, ransomware has been previously documented coming from drive-by sites and browser exploits, so even a user savvy to email attachments could still get hit. Users should make secondary backups of important files part of the daily work-flow. Options for this can be summed up with three “C”s.
- Copy files to a remote device. This is probably the best option, as long that remote device is not permanently connected to the user’s machine. Network shares that are mounted when Locky is executed will also be encrypted. Copying files to an ftp server manually (or as a scripted job for the advanced users out there) is probably the best bet.
- Create a local backup directory. During experiments researching Locky, in which our engineers continuously re-infected virtual-machines (for science), MetaFlows engineers did find that it ignores the C:\Windows directory. Do not bank on this working forever, but for now it seems like users can make a local backup directory under C:\Windows\JustInCase. If Locky strikes, it will ignore files that are stored there. This is probably the riskiest option since the malware may change its behavior at any time, but it is a clever one to use in the short-term. Of course, it also requires administrator privileges.
- Consider using USB storage. This a fantastic solution, except that people forget to unplug them once they are done backing up files. Users can plug in an external drive or usb stick, backup all necessary files, then unplug it again and Locky cannot touch it. However, if it is left it plugged in, these backups will all get encrypted just like a mounted network share.
In conclusion, Locky, like all ransomware, is a peril for all users. However, like all problems, there are solutions. Employing the MetaFlows IDS, maintaining backups, and investing in education are three of the most important tools one can use to prevent adversaries from succeeding.