 This post is a follow up to Part 1 of Taking Care of Business: Information Retention & Responsibility. Here, we will be covering items six through ten, with a wrap-up of what this document means and what we can do to help you stay secure, ethically responsible, and on the right side of the FTC’s standards.
This post is a follow up to Part 1 of Taking Care of Business: Information Retention & Responsibility. Here, we will be covering items six through ten, with a wrap-up of what this document means and what we can do to help you stay secure, ethically responsible, and on the right side of the FTC’s standards.
Item six on their list is, “Secure Remote Access to Your Network.” Their bulletin points under this heading are Ensure End Point Security, meaning that you must control who can log on remotely and determining that they are doing it safely. One way is to require two factor authentication for logins. This demands that each user have the ability to generate a token on a separate device (a cell phone) and use that in combination with a token created by a key fob. Biometrics and PINS are also considered types two-factor authentication.
The FTC would also prefer that businesses limit the amount of access that users have when away from the office. This is the part where it is useful to discuss third party access. By restricting the amount of data and the type of data that a third party or an off site worker can get to means that the truly important data has a better chance of staying safe. Offering limited, one-time access is a great way to approach giving accessibility to a third party user.
Item seven on the list is, “Apply Sound Security Practices When Developing New Products” and the first subheading asks that you “train your engineers in secure coding.” This is something tackled at the pre-design stage. It is up to your software developers to create code that is secure and will not unnecessarily put your business and clients at risk. For that to happen, they must be trained effectively on how to do so. A lack of education and foresight at this stage could be fatal before your product or service even launches.
The FTC’s second sub-heading involves following platform guidelines for security. Secure development practice guidelines are out there, and available for use. Failing to follow these can allow you to open your business up to man-in-the-middle attacks through mobile applications and other dangers. It is not a requirement that one reinvent the wheel, but instead use resources that are already available in regards to creating secure software.
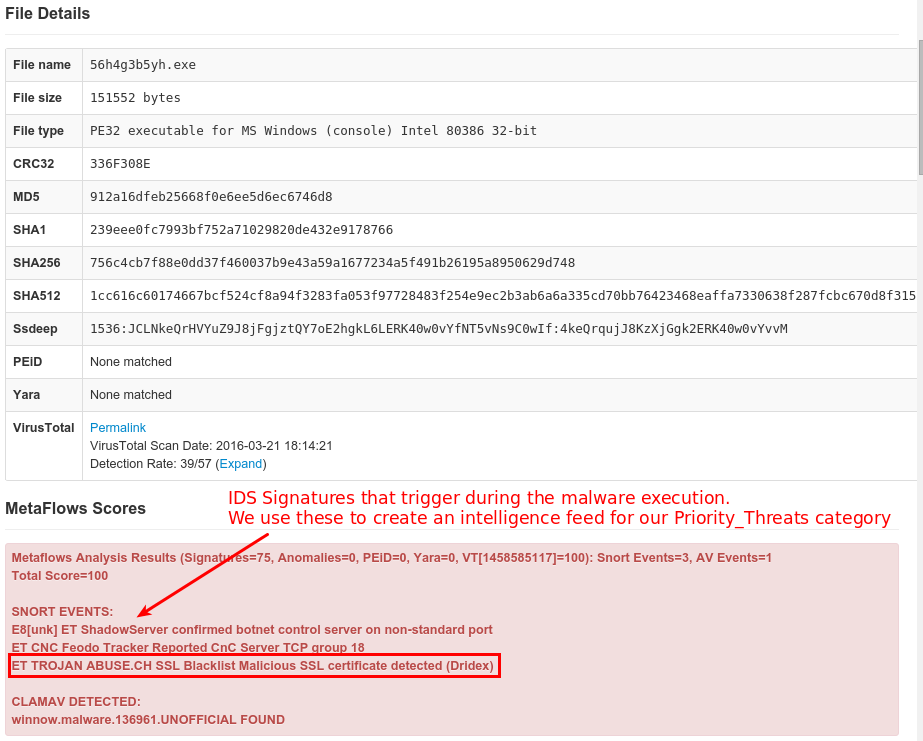
The last two bullet points are closely linked, “Verify that privacy and security features work” and “Test for common vulnerabilities.” This is something that even the big guys miss, much less the smaller companies out there. Often, it is smart to invest in an individual or company that provides penetration testing (pen testing). It is their job to try to get into your network in as many ways as possible. They will evaluate any weaknesses that exist within your code, and review the results with you. Large companies such as Microsoft and others, offer Bug Bounties, meaning that if a hacker (with their permission and under their conditions) finds a bug or security issue with their software, that hacker is rewarded and the bug can be fixed. Adobe, after some major security gaffs, has enlisted the help of the Bug Bounty program to help tighten up their software.
Issue eight of the last ten states, “Make Sure Your Service Providers Implement Reasonable Security Measures.” Since points six and seven warn you to get your software and users in line, the natural progression leads to the idea that you should evaluate anyone that you do business with. They advise that you “put it in writing” and “verify compliance.” Your security measures matter as much as the security measures of the individuals that provide you with valuable services such as connectivity and cloud computing, just to name a few. Taking someone’s word or accepting a hand-shake with the assumption that any promises they make outside of writing will be upheld is inadvisable at best. Any company’s website should list their regulatory compliance information, which is easy to verify. This is ours.
In point nine, “Put Your Procedures in Place to Keep Your Security Current and Address Vulnerabilities That May Arise,” they put their focus on not only how you go about maintaining your security practices, but also those of any third-party vendors you may work with. This is where documentation is essential, to prove that should you be summoned to court that you have been maintaining a good-faith relationship in regards to your security. Also, even after the pen-test phase, it is vital to keep on top of any perforations in your company’s defense against adversaries. If six months or nine years after a product is released, one you are responsible for, you must act upon any reports warning of a security risk with your product. Put together a way of collecting these issues and a mechanism in place to address them. Do not let them get lost in the shuffle and ignore them at your peril. This of course, also requires that you stay on top of any third-party services or vendors you may use to make sure that they are making good on their promise of security to you.
Last but not least, the FTC advises that you, “Secure Paper, Physical Media, and Devices.” Everything that was already recommended in regards to your network and digital data also applies to any hard copies. The FTC asks that you, “securely store sensitive files,” “protect devices that process personal information,” “keep safety standards in place when data is en route,” “dispose of sensitive data securely.” All of this may seem like common sense and somewhat of a no-brainer but it is worth remembering that if enterprises, both small and large, did these things the FTC would have never had to address gaffs in data containment by Rite Aid, CVS Caremark, and many unfortunate others.
We decided to use this precious blog space to bring these ten items to your attention, as it is our goal to keep you and your data safe. The MetaFlows MSS is continually evolving to help you better protect your enterprise from adversaries and the potential legal fallout from any success that they might have not had otherwise. A tired truth is that a best defense is actually a good offense and in the world of business and information security, having the right service in place can make all the difference.












 That there is a dearth of women in the Information Security (InfoSec) community is not news. The news would be if that number were to ratchet up to fifteen or twenty percent, in keeping with the growth that other STEM positions are close to hitting. Women make up only 27% of the population in Science, Technology, Engineering and Math (STEM) careers; 12% of the computer science degree holders were women according to a census in 2011. The number of women currently holding positions in Information Security is a marginal 10-12%. Even as other areas of STEM show an improvement in numbers, the Information Security field remains stagnant.
That there is a dearth of women in the Information Security (InfoSec) community is not news. The news would be if that number were to ratchet up to fifteen or twenty percent, in keeping with the growth that other STEM positions are close to hitting. Women make up only 27% of the population in Science, Technology, Engineering and Math (STEM) careers; 12% of the computer science degree holders were women according to a census in 2011. The number of women currently holding positions in Information Security is a marginal 10-12%. Even as other areas of STEM show an improvement in numbers, the Information Security field remains stagnant.